Are MCPs The New APIs?
Evaluate your spending
Imperdiet faucibus ornare quis mus lorem a amet. Pulvinar diam lacinia diam semper ac dignissim tellus dolor purus in nibh pellentesque. Nisl luctus amet in ut ultricies orci faucibus sed euismod suspendisse cum eu massa. Facilisis suspendisse at morbi ut faucibus eget lacus quam nulla vel vestibulum sit vehicula. Nisi nullam sit viverra vitae. Sed consequat semper leo enim nunc.
- Lorem ipsum dolor sit amet consectetur lacus scelerisque sem arcu
- Mauris aliquet faucibus iaculis dui vitae ullamco
- Posuere enim mi pharetra neque proin dic elementum purus
- Eget at suscipit et diam cum. Mi egestas curabitur diam elit
Lower energy costs
Lacus sit dui posuere bibendum aliquet tempus. Amet pellentesque augue non lacus. Arcu tempor lectus elit ullamcorper nunc. Proin euismod ac pellentesque nec id convallis pellentesque semper. Convallis curabitur quam scelerisque cursus pharetra. Nam duis sagittis interdum odio nulla interdum aliquam at. Et varius tempor risus facilisi auctor malesuada diam. Sit viverra enim maecenas mi. Id augue non proin lectus consectetur odio consequat id vestibulum. Ipsum amet neque id augue cras auctor velit eget. Quisque scelerisque sit elit iaculis a.

Have a plan for retirement
Amet pellentesque augue non lacus. Arcu tempor lectus elit ullamcorper nunc. Proin euismod ac pellentesque nec id convallis pellentesque semper. Convallis curabitur quam scelerisque cursus pharetra. Nam duis sagittis interdum odio nulla interdum aliquam at. Et varius tempor risus facilisi auctor malesuada diam. Sit viverra enim maecenas mi. Id augue non proin lectus consectetur odio consequat id vestibulum. Ipsum amet neque id augue cras auctor velit eget.
Plan vacations and meals ahead of time
Massa dui enim fermentum nunc purus viverra suspendisse risus tincidunt pulvinar a aliquam pharetra habitasse ullamcorper sed et egestas imperdiet nisi ultrices eget id. Mi non sed dictumst elementum varius lacus scelerisque et pellentesque at enim et leo. Tortor etiam amet tellus aliquet nunc eros ultrices nunc a ipsum orci integer ipsum a mus. Orci est tellus diam nec faucibus. Sociis pellentesque velit eget convallis pretium morbi vel.
- Lorem ipsum dolor sit amet consectetur vel mi porttitor elementum
- Mauris aliquet faucibus iaculis dui vitae ullamco
- Posuere enim mi pharetra neque proin dic interdum id risus laoreet
- Amet blandit at sit id malesuada ut arcu molestie morbi
Sign up for reward programs
Eget aliquam vivamus congue nam quam dui in. Condimentum proin eu urna eget pellentesque tortor. Gravida pellentesque dignissim nisi mollis magna venenatis adipiscing natoque urna tincidunt eleifend id. Sociis arcu viverra velit ut quam libero ultricies facilisis duis. Montes suscipit ut suscipit quam erat nunc mauris nunc enim. Vel et morbi ornare ullamcorper imperdiet.
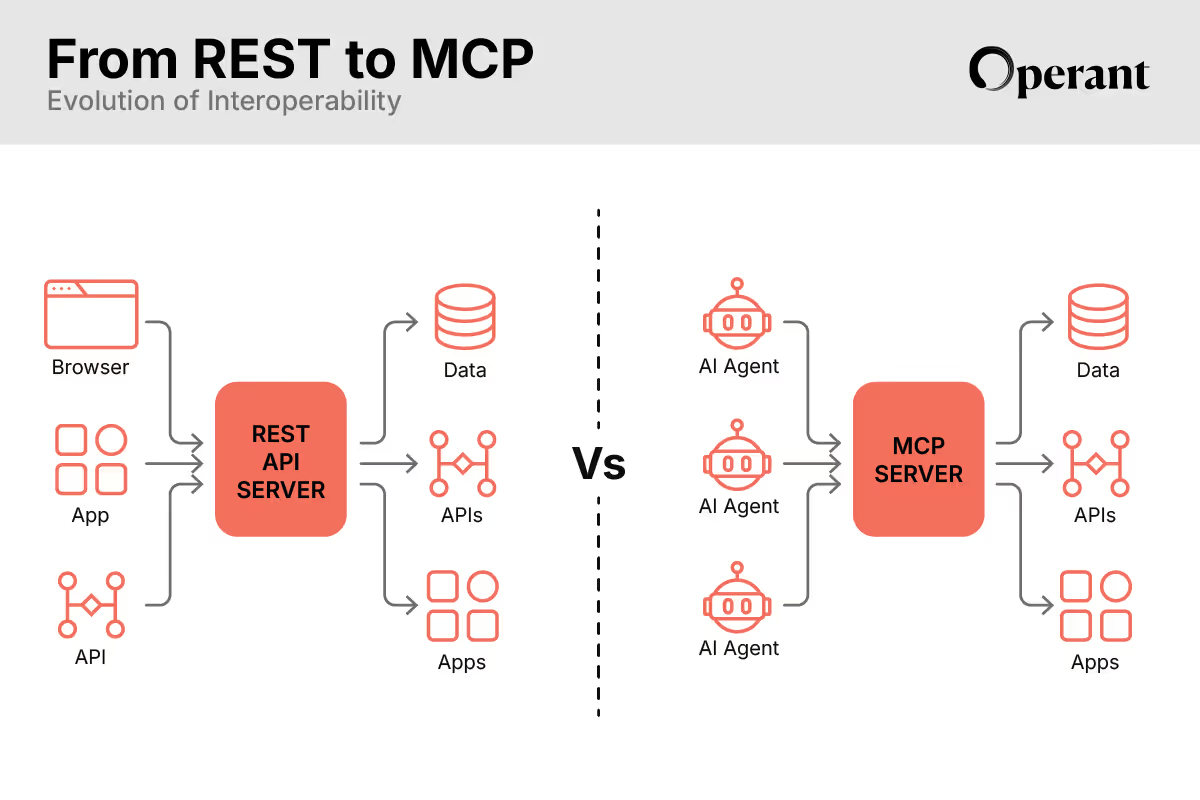
Over the past decade, APIs have revolutionized how software systems communicate. But as we move into the era of autonomous AI agents and dynamic workflows, the traditional APIs are beginning to show their limits. The way applications interact has evolved.
Enter Model Context Protocol (MCP), an AI-native interoperability framework that redefines how digital agents discover, invoke, and interact with tools and data. MCP isn't just another API standard; it's a fundamental shift in how software components, AI agents, and tools discover and communicate with each other dynamically. But with this shift comes a new set of runtime risks that traditional security approaches simply aren't built to handle.
What Is MCP, and Why Does It Matter?
MCP (Model Context Protocol) is a standardized protocol originally developed by Anthropic to allow AI agents to dynamically discover and invoke external tools and APIs using language-based interfaces.
Traditional APIs like REST were built for static, software-to-software integrations. Developers wrote documentation, built custom stubs, and expected predictable requests.
MCP is designed for autonomy, changing the entire approach.
- AI-native design: MCP speaks the language of LLMs, not the human developers. Rather than requiring developers to understand complex API documentation, agents can interact with services through natural, context-aware protocols.
- Dynamic discovery: Agents can query available tools and services at runtime, without needing hardcoded endpoints. This eliminates the unstable integration patterns.
- Natural language interfaces (NLI): Agents may interact using natural language, not just code or structured API calls. This creates a more intuitive interaction model where AI systems can discover and use tools based on natural descriptions rather than rigid API specifications.
- Autonomous interoperability: AI agents can autonomously discover, call, and combine services on the fly. This enables sophisticated workflow orchestration that adapts to changing conditions without human intervention.
In this new world, interoperability isn't a static contract; it's a living, agent-to-agent conversation. MCP serves as the universal connector that makes this dynamic interaction possible, fundamentally changing how we think about system integration.
The Revolutionary Impact of MCP
MCP addresses a critical gap in the AI ecosystem. Previously, every AI application required custom-built connections to interact with databases, APIs, and external services. This resulted in a fragmented landscape of one-off integrations that were expensive to maintain and difficult to secure.
MCP changes that by offering a secure, standardized way for AI tools to connect with data sources and services. It acts like a “USB standard” for AI, creating a universal protocol that removes compatibility headaches and simplifies development across different environments.
This standardization is already driving rapid adoption across the industry. Major platforms, including GitHub Copilot, Claude Desktop, and enterprise cloud services, are implementing MCP support, creating an expanding ecosystem of compatible tools and services.
Agents are no longer passive consumers of APIs, they have evolved into intelligent actors dynamically shaping how systems interact. This evolution introduces new risk vectors that only become apparent at runtime.
What’s Required to Secure MCP Workflows
MCP's power lies in its flexibility and dynamic nature. But that same flexibility opens the door to complex new security risks, many of which emerge only at runtime and can't be detected by traditional security tools. With agents making real-time decisions based on prompt context and tool availability, the security model must evolve.
API security has always been a complex challenge. Securing APIs was and is mainly done at the WAF, which works for basic L3 layer protection, while leaving L7 North-South monitoring as well as all East-West visibility and defenses completely unprotected. But even basic capabilities like API catalogs and detection of all-too-common ghost and zombie APIs were and are labor and resource-intensive if you try to use common tactics like VPC mirroring.
But real-time, active runtime protection, seemed beyond reach. That’s why a fundamental shift in technology was necessary to bring capabilities like blocking live API attacks as they happen and delivering full visibility into L7+ behavior, including prompt content, data movement, and tool invocation across complex workflows - these are all necessary capabilities in the modern world’s attack landscape, none of which are remotely defensible via API testing. At Operant, we were already viewing API protection in this way before AI made the importance of runtime protection that much more acute, and then came…. (drumroll, please) MCP.
MCP — the fastest and most fundamental protocol shift the modern application stack is suddenly upon us, and now it is time to secure it.
Why This Shift Is So Fundamental
MCP represents a paradigm shift from static, predetermined interactions to dynamic, autonomous communication. Traditional APIs required developers to explicitly define every endpoint, parameter, and expected behavior. With MCP, AI agents can discover and invoke tools dynamically based on natural language descriptions and contextual needs.
Traditional API security, while challenging, operated within predictable boundaries:
- You know the endpoints.
- You know the behavior patterns.
- You validate input/output schemas ahead of time.
- You can establish baseline security policies.
With MCP, the security challenge doubles because:
- Agents discover tools at runtime, expanding the attack surface dynamically.
- The context of each request can be dynamically constructed or language-based, making input validation exponentially more complex.
- Agents might chain tools in unexpected ways, creating unpredictable execution paths that bypass traditional security controls.
- The execution flow is non-deterministic, meaning threats can emerge from combinations you've never seen before.
This isn't just a new set of risks; it's a multiplication of the existing security complexity, where every traditional challenge now has dynamic, AI-driven variants:
Prompt Injection & Tool Misuse: Bad actors can manipulate agent prompts to invoke the wrong tool via MCP could leak sensitive data, misroute actions, or be tricked into unsafe behavior.
Adversarial Discovery: Malicious agents could dynamically explore your MCP-exposed services and exploit tool chains.
On-the-Fly Behavior Drift: With AI agents interpreting language-based tool descriptions, it's easier for attackers to nudge agents into unapproved behaviors.
Zero-Day-Like Exposure: Because services are dynamically described and invoked, malicious requests can't always be blocked at the API gateway level; threats happen deep in the runtime layer.
In short, the threats move as fast as the agents do. Traditional security approaches that rely on static rules and predefined attack patterns cannot keep up with the dynamic, autonomous nature of MCP-connected systems.
What Runtime Security Must Deliver for MCP
Securing MCP-connected systems requires a fundamentally different approach than traditional API security. The dynamic, autonomous nature of these systems demands specialized capabilities that can adapt as quickly as the agents themselves.
Essential Requirements for MCP Security:
Real-Time Runtime Defense: MCP security demands real-time visibility into prompt inputs, tool calls, and agent behavior. Traditional point-in-time security assessments are insufficient when agents are making autonomous decisions at runtime. Continuous monitoring is key for securing MCP.
Dynamic Toolchain Visibility: Security teams must be able to trace how agents are chaining tools together at runtime. Without this insight, it’s impossible to differentiate between legitimate workflows and manipulated behavior.
Autonomous Threat Detection: Prompt injections, jailbreaks, and integrity breaches must be detected and mitigated without disrupting valid agent activity. This requires advanced threat detection that can tell the difference between normal dynamic behavior and harmful activity.
Context Integrity Validation: Every context object passed through MCP must be validated in real-time to ensure it hasn't been tampered with or injected with malicious content. That includes semantic analysis of natural language prompts to detect injection or manipulation.
Air-Gapped Protection Capability: Enterprises operating in isolated environments need full protection without relying on external services. MCP security must function autonomously in private cloud and disconnected systems.
Multi-Environment Coverage: From GitHub Copilot and Claude Desktop to cloud-native AI services and on-prem systems, protection must extend across the entire MCP ecosystem, without compromising on consistency or depth.
Operant’s AI Gatekeeper: Purpose-Built to Meet These Needs
AI Gatekeeper’s MCP Gateway feature was purpose-built to meet these exact requirements. As the industry's first runtime security platform specifically designed for MCP-connected applications and agents, Operant provides all the essential capabilities needed to secure agentic AI workflows.
The platform delivers comprehensive protection across the entire MCP ecosystem. The feature
- Analyzes prompts and agent behavior in real-time
- Applies conditional policies to tool access
- Maps and monitors dynamic toolchains
- Detects and mitigates abnormal behavior
- Operates in cloud and disconnected deployments
Operant's approach ensures that organizations can embrace the full potential of MCP-connected AI while maintaining the security and compliance standards essential for enterprise deployment.
MCP Is the Future. Make It Secure.
MCP unlocks a modular, extensible world where AI agents can adapt in real-time to changing conditions and requirements. This represents the next evolution of enterprise software architecture, where intelligent agents orchestrate complex workflows autonomously.
But without proper security, this flexibility becomes a critical liability. Traditional API protection is still needed, but for MCP, it’s just the starting point. The real challenge is at runtime, where agents reason, decide, and act.
Securing MCP doesn’t need a redesign of the architecture; it just needs to have the right layer of protection that sees what’s happening, when it’s happening.
Operant provides that layer that helps you embrace the future of AI interoperability — securely, autonomously, and at runtime.
Don’t trust tools by default. Discover, Detect & Defend them at runtime. We invite you to try Operant AI Gatekeeper to see for yourself how easy comprehensive security can be for your entire AI application environment.
Sign up for a 7-day free trial to experience the power and simplicity of AI Gatekeeper's 3D AI Security for yourself.



3%20%3D(Art)Kubed%20(16%20x%209%20in)%20(7)-p-1080.avif)




.png)
.png)
