API & Cloud Protector
3D Runtime Defense that works beyond the WAF
Active Threat Protection For APIs & Cloud
Bring API Security beyond the WAF with runtime protection for every API, service, and interaction Internal to External and Ingress to Egress

The only Gartner® Featured Vendor across 5 critical AI Security categories in 2025
Operant AI is the only vendor featured across all five of Gartner®'s most critical AI security reports, demonstrating our unique depth and breadth in securing the full spectrum of AI, LLM, API, MCP, and Agent deployments.
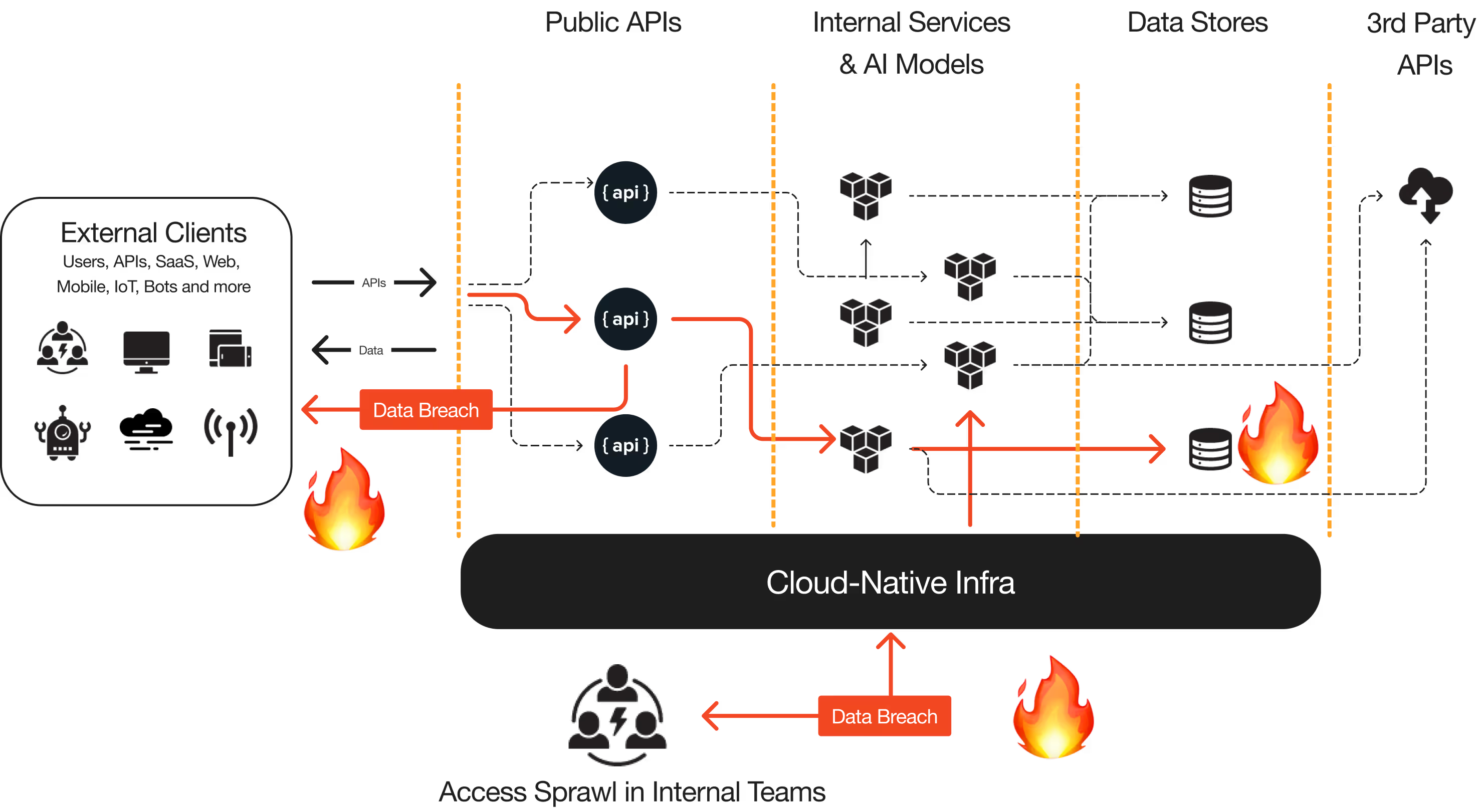
Modern threats don't stay at one layer, discover and protect the entire attack surface from APIs to Cloud

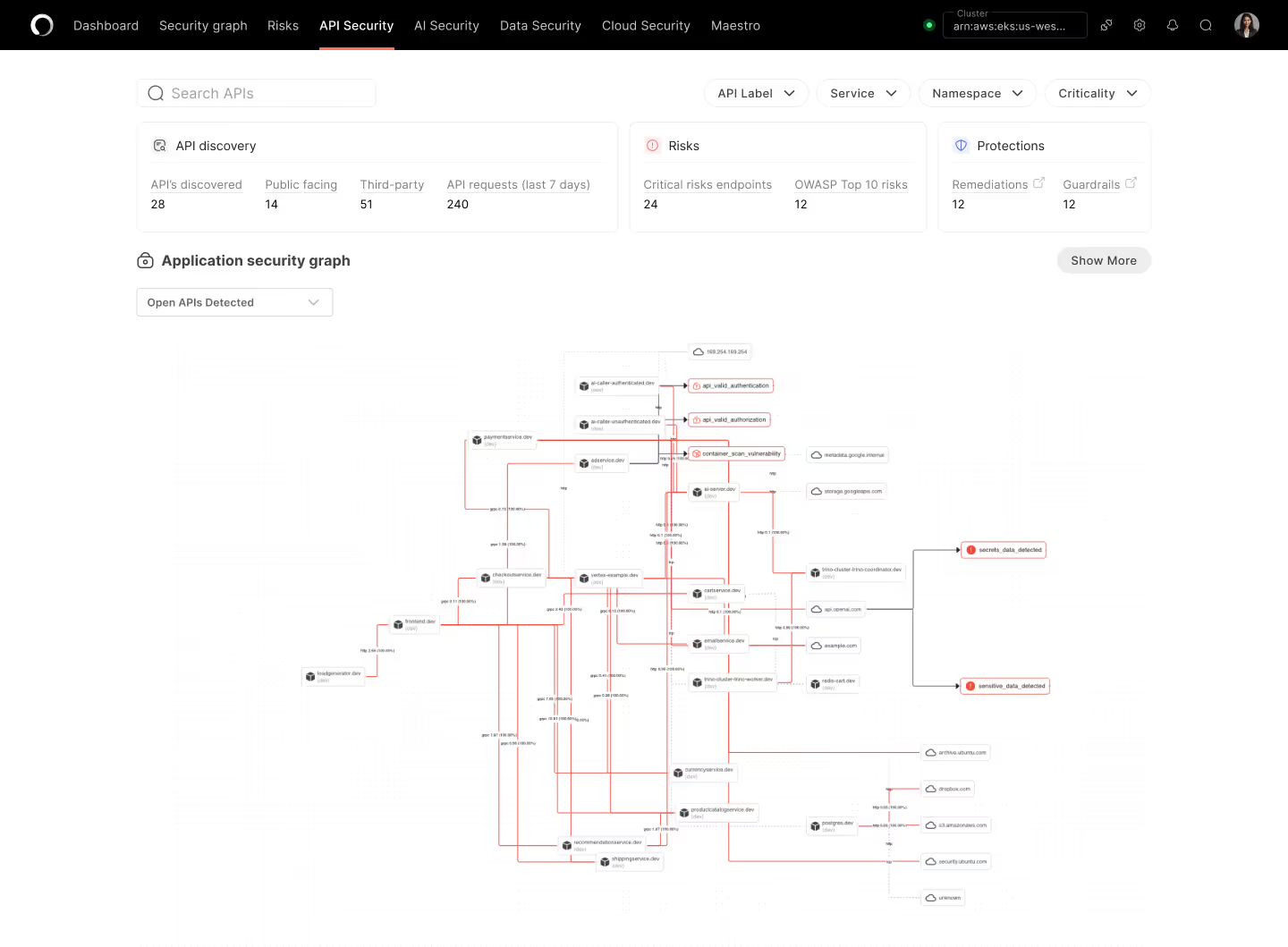
Real-time Discovery across Every Layer
This is some text inside of a div block.
Stop wasting time on static scanners and manual API testing, get automatic API catalogs, real-time insights on vulnerabilities, and prioritized runtime risks from internal, legacy and third party APIs.

Open API Graphs & Attack Paths
This is some text inside of a div block.
Get an instant view of your entire live API blueprint, across dev, staging and prod. With an intuitive graph interface, fly through risk, context, and threat models for public and internal API endpoints.

Inline Threat Protection for APIs and Kubernetes
This is some text inside of a div block.
API protection doesn't have to stop at a WAF. Protect your internal and 3rd party API interactions with K8s-native controls for protocol specific authentication, authorization, traffic rate limiting, API to API microsegmentation, and more.
CLOUD SECURITY LEADERSHIP
Download The Cloud Security Report by Latio
"Operant’s approach to runtime AI application security is truly holistic by defending APIs, applications, agents, and containers all at the same time, offering one stop for meaningful workload protection."
- James Berthoty
 Download the Report
Download the ReportSave time and money while securing your entire cloud-native nervous system from AI to APIs

Make Every API More Secure
This is some text inside of a div block.
Actively protect against internal and 3rd party API abuses and attacks within the application itself. With absolutely no manual work, discover the entire live API blueprint - zombies and known APIs alike - and eliminate critical threats directly within Operant’s interface without any extra engineering projects.

Do More With Less
This is some text inside of a div block.
Know everything you need to know about your APIs across your entire cloud application stack without any integrations, instrumentation or manual upkeep. Eliminate manual API catalogs, overly generic rulesets and manual remediation workflows by enforcing fine-grained security policies across every API in your stack with zero drift.

Reduce Costs & Tooling Overload
This is some text inside of a div block.
Eliminate the cost of installation, integrations, maintenance, training, and tooling upkeep while being more secure. Avoid the cost, overhead, and technical debt from VPC mirroring solutions that don’t even block OWASP attacks. Reduce the burden on your SOC with active runtime defense via purpose-built OWASP and MITRE guardrails.

Scale Applications Faster
This is some text inside of a div block.
Don’t let API risks hold your application development timelines back. Operant shields every layer of your Kubernetes-based applications against major API-based attacks and scales automatically as you grow. Deploy faster and more securely with full knowledge of your API footprint + security guardrails that protect your applications from dev to staging to prod.



3%20%3D(Art)Kubed%20(16%20x%209%20in)%20(7)-p-1080.avif)



.png)