K8s-Native Security for K8s-Native Apps
Operant shields your Kubernetes clusters in real-time
Operant Unifies Full K8s Discovery, Detection and Defense in a Single Solution
Complexity and ephemerality make K8s attack paths exponentially harder to defend

Automatic KSPM
K8s-Native NHI Security
Runtime Threat Deterrence
The CSPM++ you need for K8s-native apps. Default configs of K8s Infra leaves major open security gaps. Operant's automatic KSPM natively understand the ephemerality and relationships of all K8s layers at any scale.
K8s permissions are insecure by default and overpermissioning leaves applications open to attacks. Operant's K8s Identity and Entitlement Management enforces access controls across pods, namespaces, services and clusters.
Moving beyond static container scanning, Operant's runtime threat deterrence identifies, flags, and prioritizes threats based on live K8s telemetry across the entire cluster and actively shields your clusters.
Skip the POC.
Deploy Operant Today.
Single step helm install.
Zero instrumentation. Zero Integrations.
Works in <5 minutes.
Save time and money while protecting your entire K8s footprint
Active Protection for the Entire Product
Amplify Security Without More Work
Reduce Costs & Complexity
Accelerate Business Growth
Enterprise Ready
K8s-Security
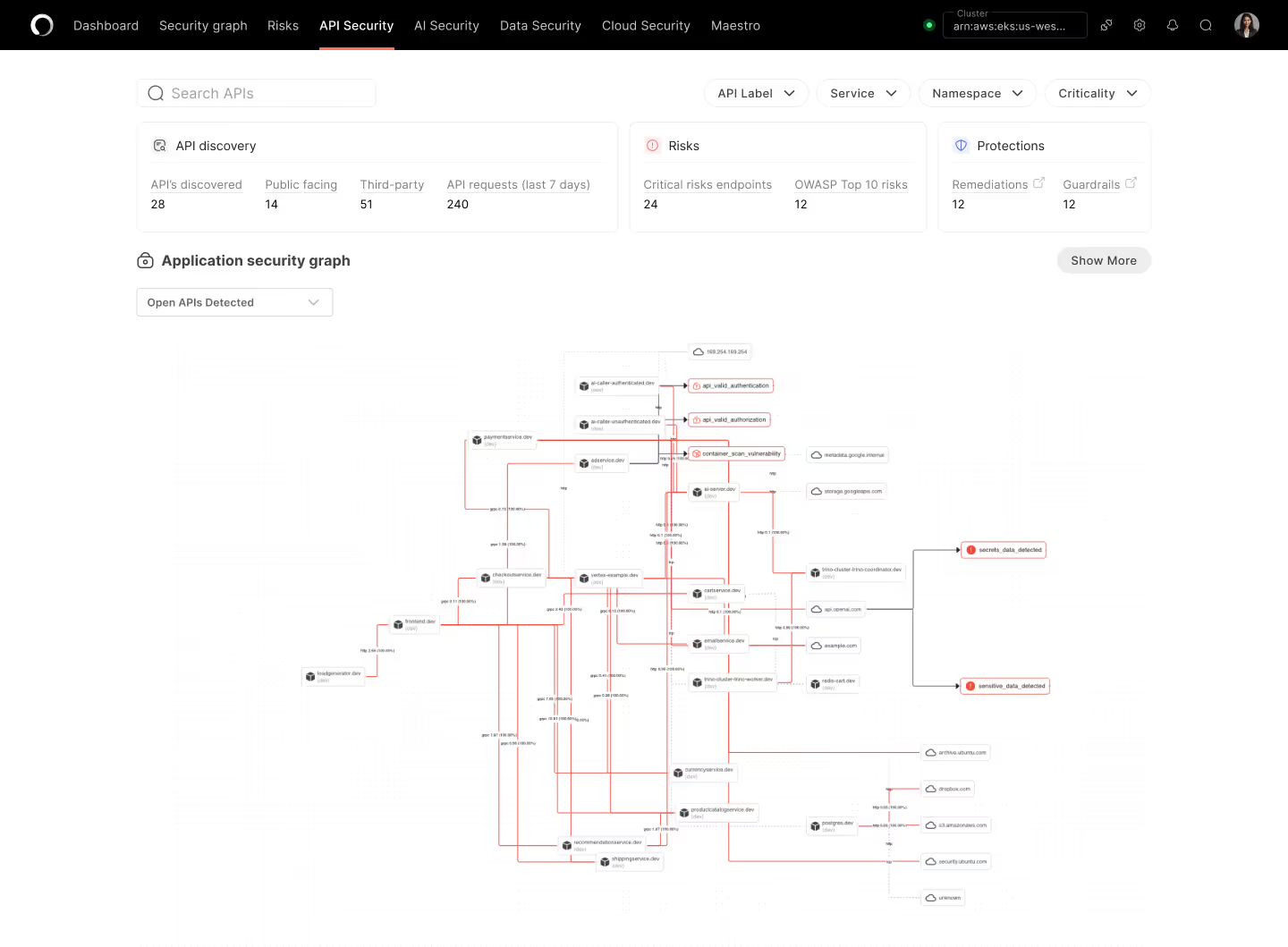
The lines between cloud infra and applications are illusions
Operant crosses the invisible barrier to protect cloud applications in their native environments across every layer from infra to L7+, from prompts to processes.
Single-Step, Zero-Instrumentation Deployment
Deploy in minutes without the need for complex integrations or instrumentation, so you can see value immediately without impacting workflows.
Purpose-Built for Cloud-Native Environments
Operant integrates seamlessly into Kubernetes and other cloud-native infrastructure, enabling proactive, frictionless defense where data breaches actually happen.




3%20%3D(Art)Kubed%20(16%20x%209%20in)%20(7)-p-1080.avif)







