“Anti-Virus” for MCP: Part 1

Evaluate your spending
Imperdiet faucibus ornare quis mus lorem a amet. Pulvinar diam lacinia diam semper ac dignissim tellus dolor purus in nibh pellentesque. Nisl luctus amet in ut ultricies orci faucibus sed euismod suspendisse cum eu massa. Facilisis suspendisse at morbi ut faucibus eget lacus quam nulla vel vestibulum sit vehicula. Nisi nullam sit viverra vitae. Sed consequat semper leo enim nunc.
- Lorem ipsum dolor sit amet consectetur lacus scelerisque sem arcu
- Mauris aliquet faucibus iaculis dui vitae ullamco
- Posuere enim mi pharetra neque proin dic elementum purus
- Eget at suscipit et diam cum. Mi egestas curabitur diam elit
Lower energy costs
Lacus sit dui posuere bibendum aliquet tempus. Amet pellentesque augue non lacus. Arcu tempor lectus elit ullamcorper nunc. Proin euismod ac pellentesque nec id convallis pellentesque semper. Convallis curabitur quam scelerisque cursus pharetra. Nam duis sagittis interdum odio nulla interdum aliquam at. Et varius tempor risus facilisi auctor malesuada diam. Sit viverra enim maecenas mi. Id augue non proin lectus consectetur odio consequat id vestibulum. Ipsum amet neque id augue cras auctor velit eget. Quisque scelerisque sit elit iaculis a.

Have a plan for retirement
Amet pellentesque augue non lacus. Arcu tempor lectus elit ullamcorper nunc. Proin euismod ac pellentesque nec id convallis pellentesque semper. Convallis curabitur quam scelerisque cursus pharetra. Nam duis sagittis interdum odio nulla interdum aliquam at. Et varius tempor risus facilisi auctor malesuada diam. Sit viverra enim maecenas mi. Id augue non proin lectus consectetur odio consequat id vestibulum. Ipsum amet neque id augue cras auctor velit eget.
Plan vacations and meals ahead of time
Massa dui enim fermentum nunc purus viverra suspendisse risus tincidunt pulvinar a aliquam pharetra habitasse ullamcorper sed et egestas imperdiet nisi ultrices eget id. Mi non sed dictumst elementum varius lacus scelerisque et pellentesque at enim et leo. Tortor etiam amet tellus aliquet nunc eros ultrices nunc a ipsum orci integer ipsum a mus. Orci est tellus diam nec faucibus. Sociis pellentesque velit eget convallis pretium morbi vel.
- Lorem ipsum dolor sit amet consectetur vel mi porttitor elementum
- Mauris aliquet faucibus iaculis dui vitae ullamco
- Posuere enim mi pharetra neque proin dic interdum id risus laoreet
- Amet blandit at sit id malesuada ut arcu molestie morbi
Sign up for reward programs
Eget aliquam vivamus congue nam quam dui in. Condimentum proin eu urna eget pellentesque tortor. Gravida pellentesque dignissim nisi mollis magna venenatis adipiscing natoque urna tincidunt eleifend id. Sociis arcu viverra velit ut quam libero ultricies facilisis duis. Montes suscipit ut suscipit quam erat nunc mauris nunc enim. Vel et morbi ornare ullamcorper imperdiet.
As MCP becomes the backbone for modern AI interoperability, security teams are facing a new, urgent reality. MCP interfaces are popping up everywhere, from GitHub Copilot plugins on developer machines to open-source orchestration tools deployed across Kubernetes clusters. But there's one catch: no two MCP environments look the same.
Securing MCP is not about protecting a single point of failure. It's about defending an ever-evolving ecosystem of AI agents, tools, and data flows. This complexity creates a need for security that works across environments and contexts, protecting the live assets as they interact with their dynamic, probabilistic environments.
Bringing Order to Chaos: Securing a moving target across MCP users, clients, and apps
MCP clients and servers operate in fast-changing environments that differ significantly from traditional web applications. They need to handle various types of data, connect to multiple tools and systems, and support AI agents making decisions in real-time.
Unlike traditional servers that primarily serve static content or well-defined APIs, MCP servers must dynamically process context, manage multiple concurrent AI sessions, and adapt to different model requirements in real-time. This creates unique security challenges and exposes an attack surface that is significantly different from anything security teams have encountered before.
Suddenly, tool poisoning, prompt injection, and rogue agents have become threats from within the environment itself, while the distribution of users accessing various MCP servers and tools without a clear security approval or governance process has quickly ballooned, making basic governance almost impossible. While a developer might interact with three MCP servers on Monday as they build out a project, they might change their mind and interact with three others by Thursday.
This type of dynamism in the attack surface across users + tools + 3rd parties + data defies traditional categories of security tactics. It makes static efforts of containment futile, but ironically, there is one analogy from the old pre-AI world that can help us understand how to approach it in a lasting way: Anti-virus for MCP.
Just as organizations realized many years ago that they could never fully stop employees from being duped by phishing attacks, and therefore they needed a uniform set of controls that would reduce the attack surface and the risk even as the interactions themselves changed constantly (think: original desktop anti-virus software), now is a time when a similar mindset for MPC security can keep the benefits of productivity that AI & MCP have to offer while reducing the level of open chaos and threats that are currently swirling around in these insecure, ungoverned, dynamic environments.
Every MCP Server Is Unique and Workflows Are Dynamic by Design
MCPs are built to enable autonomous agents to select, invoke, and chain tools in real-time. This means workflows aren't statically defined; they emerge during runtime based on agent decisions and evolving context. Quite likely that, one run after the other might be different, since several non-deterministic systems are involved.
Security tools must be context-aware and dynamically detect:
- Which agents are invoking which tools and why
- What data is being shared across the context boundary
- How toolchains are constructed and whether they're being manipulated
- When agent behavior deviates from established patterns
Rigid security frameworks can't keep up with this diversity. A flexible defense system must adapt to different MCP configurations without breaking the pipeline or delaying deployment. Without flexible detection logic that understands natural language interactions and behavioral baselines, threats like jailbreaks, tool spoofing, and prompt injections will go unnoticed until the damage is done.
Evolving Threat Landscape
As AI systems become more sophisticated, so do the attack vectors targeting them. Attackers are already exploiting:
- Context leakage across agent boundaries, where sensitive information bleeds between different AI workflows
- Over-permissioned tool access allows agents to perform actions beyond their intended scope
- Agentic privilege escalation, where compromised agents gain unauthorized system access
- Tool poisoning and dependency confusion in open-source MCP servers
- Semantic manipulation through carefully crafted prompts that bypass traditional security filters
Static security measures cannot anticipate these novel attack methods that specifically target AI-mediated interactions.
Phased Approach of MCP Adoption
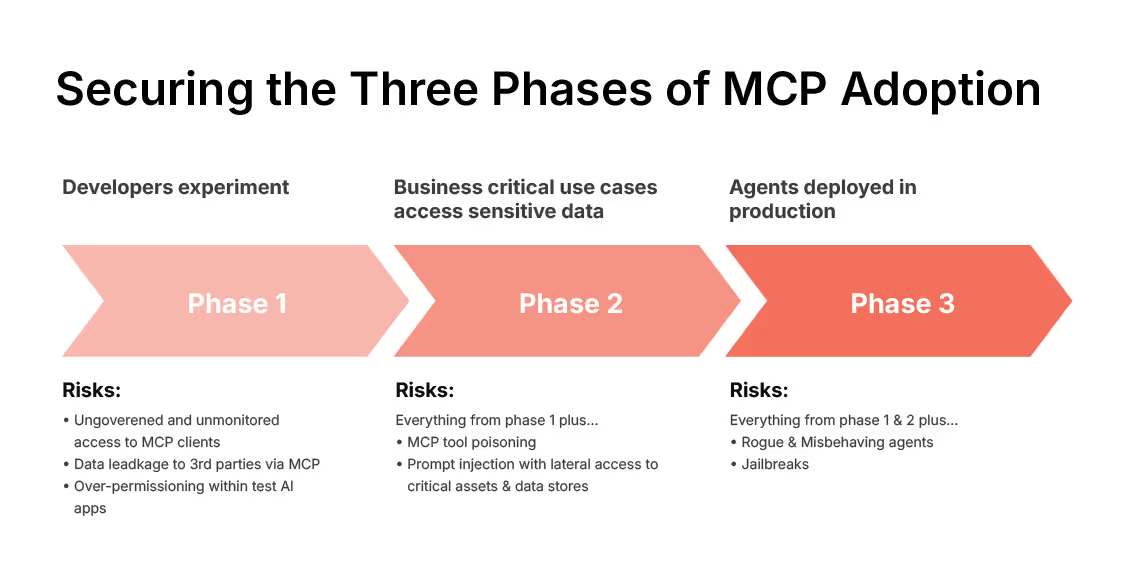
The adoption of Model Context Protocol (MCP) is unfolding in three distinct phases, each marked by a dramatic shift in scale, sensitivity, and security risk. In the initial developer phase, MCP serves as an experimental playground where individual developers deploy servers locally on their workstations to test AI capabilities with personal productivity tools. During the initial developer experimentation phase, organizations face foundational risks including ungoverned and unmonitored access to MCP clients, potential data leakage to third parties, and over-permissioning within test AI applications. While these risks may seem manageable in isolated development environments, they establish dangerous precedents if left unaddressed.
As MCP adoption matures, it enters a second, far more critical phase: integration into business-sensitive environments. Here, MCP servers no longer operate in isolation. Teams begin using shared infrastructure that connects to sensitive systems like customer databases, cloud storage, and internal APIs. As MCP deployments mature into the business-critical phase, all previous risks persist while new threats emerge, including MCP tool poisoning and prompt injection attacks that can provide lateral access to critical assets and data stores.
The final mainstream phase marks MCP's evolution from a development tool to an enterprise-wide platform that extends beyond technical teams to serve business users directly. Here, MCP goes fully mainstream, embedded in enterprise-scale, agentic applications across departments. At this point, MCP is no longer a developer playground, it becomes the backbone of mission-critical operations, requiring the same rigor and runtime defense as any other enterprise system. As MCP powers enterprise-wide agentic applications, the environment is ripe for rogue or misbehaving agents to become a significant concern when AI systems operate autonomously across mission-critical infrastructure, while sophisticated jailbreak attempts can compromise entire MCP implementations.
This cumulative risk model demonstrates why early-stage security planning is crucial. Organizations cannot simply bolt on security measures after reaching enterprise deployment. Instead, they must establish robust governance frameworks, monitoring systems, and access controls from the very first developer experiments. The exponential growth in risk exposure from phase to phase underscores the importance of treating MCP security as a foundational requirement rather than an afterthought, ensuring that experimental enthusiasm doesn't compromise long-term organizational security posture.
In the second part we’ll explore the core principles of securing MCP environments and highlight the most effective tools for the job.



3%20%3D(Art)Kubed%20(16%20x%209%20in)%20(7)-p-1080.avif)




.png)

