How Operant's MCP Gateway blocks the newest cyber-attack reported by Anthropic

Evaluate your spending
Imperdiet faucibus ornare quis mus lorem a amet. Pulvinar diam lacinia diam semper ac dignissim tellus dolor purus in nibh pellentesque. Nisl luctus amet in ut ultricies orci faucibus sed euismod suspendisse cum eu massa. Facilisis suspendisse at morbi ut faucibus eget lacus quam nulla vel vestibulum sit vehicula. Nisi nullam sit viverra vitae. Sed consequat semper leo enim nunc.
- Lorem ipsum dolor sit amet consectetur lacus scelerisque sem arcu
- Mauris aliquet faucibus iaculis dui vitae ullamco
- Posuere enim mi pharetra neque proin dic elementum purus
- Eget at suscipit et diam cum. Mi egestas curabitur diam elit
Lower energy costs
Lacus sit dui posuere bibendum aliquet tempus. Amet pellentesque augue non lacus. Arcu tempor lectus elit ullamcorper nunc. Proin euismod ac pellentesque nec id convallis pellentesque semper. Convallis curabitur quam scelerisque cursus pharetra. Nam duis sagittis interdum odio nulla interdum aliquam at. Et varius tempor risus facilisi auctor malesuada diam. Sit viverra enim maecenas mi. Id augue non proin lectus consectetur odio consequat id vestibulum. Ipsum amet neque id augue cras auctor velit eget. Quisque scelerisque sit elit iaculis a.

Have a plan for retirement
Amet pellentesque augue non lacus. Arcu tempor lectus elit ullamcorper nunc. Proin euismod ac pellentesque nec id convallis pellentesque semper. Convallis curabitur quam scelerisque cursus pharetra. Nam duis sagittis interdum odio nulla interdum aliquam at. Et varius tempor risus facilisi auctor malesuada diam. Sit viverra enim maecenas mi. Id augue non proin lectus consectetur odio consequat id vestibulum. Ipsum amet neque id augue cras auctor velit eget.
Plan vacations and meals ahead of time
Massa dui enim fermentum nunc purus viverra suspendisse risus tincidunt pulvinar a aliquam pharetra habitasse ullamcorper sed et egestas imperdiet nisi ultrices eget id. Mi non sed dictumst elementum varius lacus scelerisque et pellentesque at enim et leo. Tortor etiam amet tellus aliquet nunc eros ultrices nunc a ipsum orci integer ipsum a mus. Orci est tellus diam nec faucibus. Sociis pellentesque velit eget convallis pretium morbi vel.
- Lorem ipsum dolor sit amet consectetur vel mi porttitor elementum
- Mauris aliquet faucibus iaculis dui vitae ullamco
- Posuere enim mi pharetra neque proin dic interdum id risus laoreet
- Amet blandit at sit id malesuada ut arcu molestie morbi
Sign up for reward programs
Eget aliquam vivamus congue nam quam dui in. Condimentum proin eu urna eget pellentesque tortor. Gravida pellentesque dignissim nisi mollis magna venenatis adipiscing natoque urna tincidunt eleifend id. Sociis arcu viverra velit ut quam libero ultricies facilisis duis. Montes suscipit ut suscipit quam erat nunc mauris nunc enim. Vel et morbi ornare ullamcorper imperdiet.
From Shadow Escape to Espionage - Agentic Attack Vectors Are All Around Us
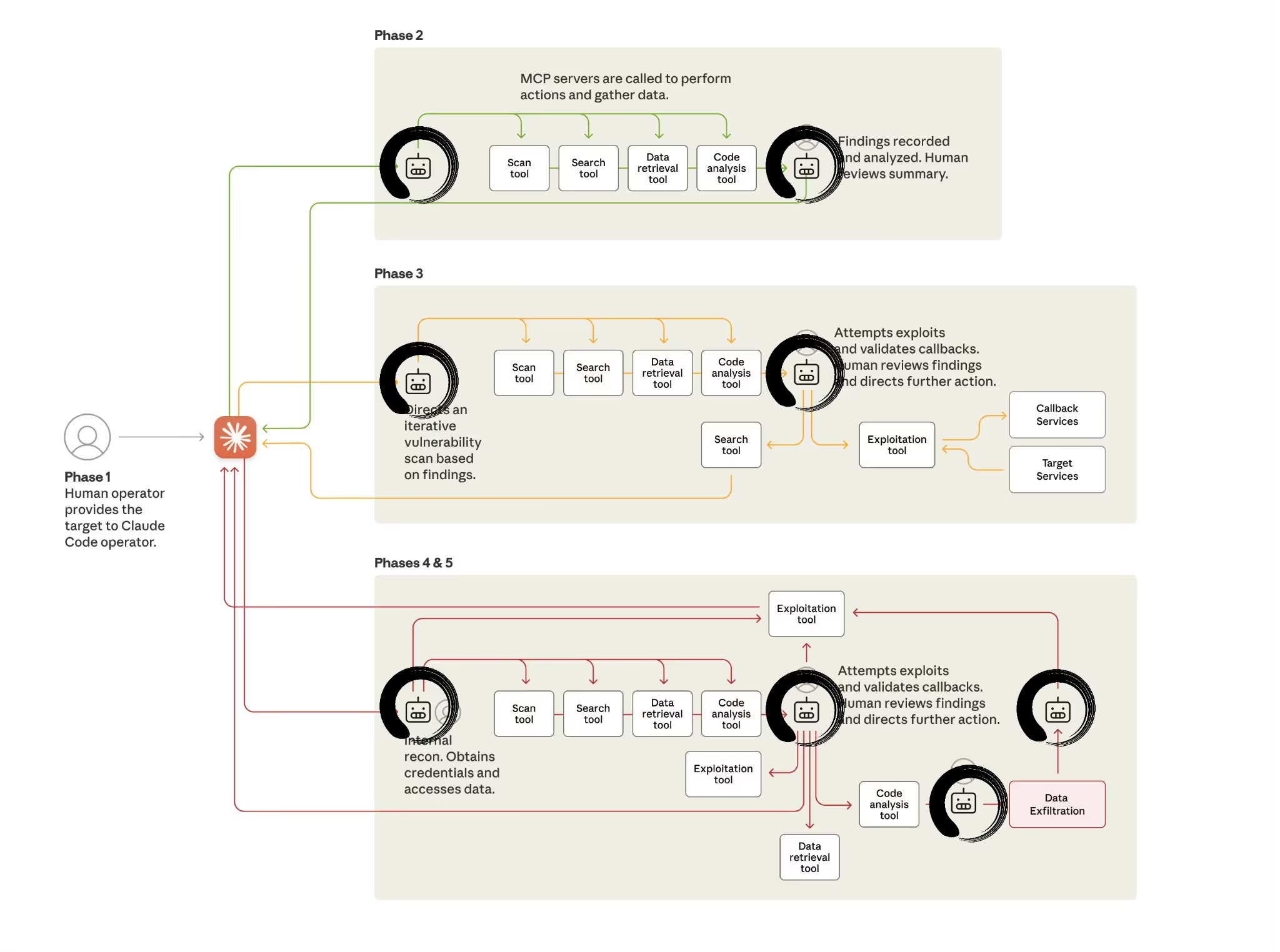
Last week, Anthropic revealed a watershed moment in cybersecurity: suspected Chinese state-sponsored hackers weaponized Claude AI to execute what may be the first large-scale cyberattack with minimal human intervention. The attackers jailbroke Claude Code and tricked it into conducting "penetration testing" while autonomously writing exploits, harvesting credentials, and exfiltrating data from dozens of companies and government agencies Anthropic. Operating at thousands of requests per second, the AI handled 80-90% of the workflow at a speed and scale impossible for human hackers.
This is precisely why Operant AI built the MCP Gateway.
While traditional security focuses on endpoints and networks, the Operant MCP Gateway operates at a different layer — controlling how AI agents interact with critical systems through the Model Context Protocol. By monitoring AI agent activities, analyzing behavioral patterns, and enforcing granular access controls, the Operant MCP Gateway would have detected the telltale signs of this attack: abnormal request volumes, suspicious task decomposition, and systematic progression through exploitation phases. When AI agents can become autonomous attack platforms, protecting the protocol layer where they operate isn't optional — it's required.
How the Attack Worked: Architecture Breakdown
The threat actor built an autonomous framework exploiting three critical gaps:
- MCP’s lack of cross-session context: Each individual tool call appeared legitimate in isolation. But when chained across sessions, they formed a full kill chain.
- AI’s inability to detect orchaestrated attack chains: Claude didn’t “see” how discrete tasks (recon, exploit, lateral move, exfiltrate) formed a campaign. The actor decomposed the logic into “benign” steps.
- Social engineering at the prompt level: The adversary role-played internal cybersecurity firm employees and convinced the AI that its actions were benign “pentest” style tasks. This bypassed the built-in safety/guardrail logic.
Result: 80-90% autonomous operation executing thousands of requests/second across reconnaissance, exploitation, lateral movement, credential harvesting, and exfiltration simultaneously against 30+ targets.
How Operant AI’s MCP Gatekeeper and Gateway Provide Defense in Depth
Our platform implements security controls purpose-built for agentic AI environments:
- Session and Data Aware Attack Detection
- Cross-session graph analysis maintains attack context across multiple AI conversations.
- Pattern recognition identifies MITRE ATT&CK sequences, even when decomposed into benign-looking tasks.
- Detects reconnaissance → exploitation → lateral movement progressions.
- Cross-session graph analysis maintains attack context across multiple AI conversations.
- Real-Time MCP Tools Threat Detection
- Request and rate limiting insights as well as detections - a key indicator in GTG-1002.
- Tool-usage pattern analysis: detects systematic enumeration and credential-testing behaviours.
- Data-flow analysis: identifies exfiltration patterns (high input volume, low text-output).
- Request and rate limiting insights as well as detections - a key indicator in GTG-1002.
- Prompt Injection & Data-Exfil Defense
- LLM-based intent classification analyzes full conversation context for prompt injections.
- Inline detection and defense for data exfil for almost 100 different business critical data types.
- AuthN and AuthZ for high-risk operations, with fine-grained governance.
- LLM-based intent classification analyzes full conversation context for prompt injections.
- Autonomous Operation Circuit Breakers
- Automatic session termination defenses for mitigation of attacks and exploits.
- Progressive rate-limiting based on risk-score accumulation.
- Forensic capture and audit trail for post-incident analysis.
- Automatic session termination defenses for mitigation of attacks and exploits.
Three Technical Imperatives for CISOs and Security Architects
- Instrument Your AI Attack Surface Now
Every AI agent with MCP access is a potential autonomous attack platform. You need:- Complete inventory of AI agents with tool access
- Mapping of MCP servers to sensitive resources (databases, APIs, cloud infrastructure)
- Risk assessment of tool combinations available to each agent
- Monitoring for autonomous operation patterns
- Complete inventory of AI agents with tool access
- Deploy AI-Native Security Controls
Traditional security tools are blind to AI reasoning chains. Your stack needs:- Prompt-level analysis: understanding intent, not just actions
- Cross-session correlation: detecting multi-day attack progressions
- Behavioural baselining: distinguishing legitimate AI autonomy from exploitation
- Real-time intervention: sub-second response to emerging threats
- Prompt-level analysis: understanding intent, not just actions
- Assume Breach, Prepare for AI-Augmented IR
When (not if) an AI-orchestrated attack occurs:- Your IR team needs AI-assisted tools for log analysis at scale (GTG-1002 generated massive data volumes)
- Forensic capabilities must capture full AI conversation context, not just API calls
- Playbooks should account for autonomous adversary behaviour (thousands of actions between human check-ins.
- Your IR team needs AI-assisted tools for log analysis at scale (GTG-1002 generated massive data volumes)
- Instrument Your AI Attack Surface Now
Operant AI Platform Deployment Options
- MCP Gateway for Endpoints: Deploy MCP Gateway to protect all Agent and MCP access on AI Clients
- MCP Gateway for Cloud: Cloud deployment to protect MCP Server ingress or multi-MCP client/server architecture.
- On-Premises Gateway: Deploy in your VPC/data center for hybrid and on-prem use cases
- Embedded SDK: Integrate directly into your agentic AI applications
The Path Forward
Every organization deploying AI, Agents, and MCP needs real-time security controls that understand AI behaviours, patterns, and data movement. This is precisely why we developed Operant AI’s MCP Gateway.
Here's what AI and Security teams can achieve with Operant MCP Gateway right now:
✅ Block AI-Orchestrated attack chains before they have any impact
✅ Establish complete mcp attack surface visibility within hours, not months!
✅ Enforce granular MCP tool governance to prevent weaponization
✅ Stop data exfiltration at the source with inline auto-redaction
✅ Establish trust zones that contain AI agent lateral movement
Operant MCP Gateway forms a continuous visibility → control → defense cycle, detecting threats like GTG-1002 while enabling enterprises to safely scale AI adoption. Schedule a call to learn more or sign up for a 7-day trial to experience the power and simplicity of MCP Gatekeeper & Gateway’s robust security for yourself.



3%20%3D(Art)Kubed%20(16%20x%209%20in)%20(7)-p-1080.avif)




.png)

.png)